If you’ve been in IT longer than 20 minutes, no doubt you’ve heard of MDR (Managed Detection and Response) and wondered not just what it is, but if it's a service you need to consider for your organization. The simple answer is: this is a great technology, and depending on the size and maturity of your organization, you may want to consider MDR as a cybersecurity technology choice.
Here’s an MDR definition put forth by Gartner®:
Market Guide for Managed Detection and Response Services, Published 14 February 2023
MDR is most appropriate for Small-to-Medium Businesses (SMBs <500-1500 employees). Most enterprise level organizations have large IT staffs, whereas SMBs generally have small, frequently overworked IT staffs of 3-5 people. These small IT teams need in-depth visibility into their environment. Some may have security tools to help them protect their environment such as MFA (Multi-Factor Authentication) or AV/EDR (Antivirus/EndPoint Detection and Response), but none of these teams have the bandwidth to properly manage these solutions alone.
MDR, What is it? And how are others using that term
Managed EDR tools have been explained as MDR solutions by many vendors. The truth is that these vendors use the term “MDR” to simply refer to a security product being managed by a third party outside your organization. One of the very common scenarios where this is seen is a managed AV/EDR solution focused primarily on the endpoint network (securing an organization's laptop/desktops from malware).
For the purpose of this blog, we focused on MDR solutions that provide an outsourced SOC (Security Operations Center) capability. This will help companies meet the centralized logging and monitoring requirements that are foundational to most compliance frameworks along with auditing of high priority accounts. In this capacity, MDR includes both foundational technology to collect, store, and analyze event log data, paired with professional services of an analyst team to lend their cybersecurity expertise to the investigation of alerts as they occur.
QOMPLX MDR provides the following benefits and differentiators:
- Log collection and correlation by integrating with existing data sources, both on-prem or cloud with data sources like AWS, or O365
- Over 300+ pre-built directions, with the support of the Analyst Team to assist with custom content creation as well as responding and investigating incidents that might arise
- Scheduled reporting and staff meetings to ensure teams are kept abreast of what is happening in their environment
- EASM Technology to monitor your public facing attack surface, a feature that many other MDR vendors simply do not offer today
- Monitoring of the environment is performed 24x7x365 by the SOC
A common strategy for MDR vendors is to wrap their capability with an EDR tool, thereby the SIEM function is a separate product\solution purchase. Integration with other existing solutions generally has an additional dollar value increase to the overall cost of implementation.
The EDR based solution, in general, has a much larger footprint as it needs to be deployed to each managed endpoint. The QOMPLX MDR solution deploys minimal assets in the environment while still providing broad log collection coverage. A QOMPLX MDR solution can provide several benefits (this is not a comprehensive list):
- It can offload some of the daily workload (specifically event monitoring) to a trusted third party or SOC operator
- Active Directory can be continuously examined and its vulnerabilities reported
- Active remediation can be done on selected events (leveraging functional integration with existing technology in the environment), escalating\assigning the more serious events for IT staff intervention
- Events can be researched prior to assignment so they can be enriched with additional details
- If there is integration with a workflow management\Help Desk function, incident tickets can be generated for tracking purposes
- It can provide alerts and\or escalations depending on event severity
The list goes on.
An MDR solution also has economic advantages. To create and properly staff an in-house SOC function is going to be an expensive solution because of the following reasons:
- Additional staff will have to be hired and trained
- A facility will have to be built-out and equipped
- Software of some sort will have to be purchased, configured and personnel trained to operate it
This is not an all inclusive list of costs, but these costs are generally higher than the purchase price\subscription cost of the MDR solution. When considering an MDR solution, it is important to understand these items have already been addressed and are provided as part of the overall solution so it's more cost effective.
In a large enterprise many of these costs can be mitigated by redeploying existing assets (people, equipment, re-configuring an existing part of the facility), but there will still need to be additional personnel hired to fill out a 3 shift coverage model. The cost of purchasing, training, and maintaining supporting software will have to be considered.
Clearly, if the IT staff is modest in size and\or resources are constrained, MDR is a viable option with a significant upside.
Below is a graphic which shows the different aspects of functionality an MDR platform provides. You will notice that while endpoint monitoring capabilities are not mentioned, they can be included with Third Party Integration as a data source, which is typically the case.
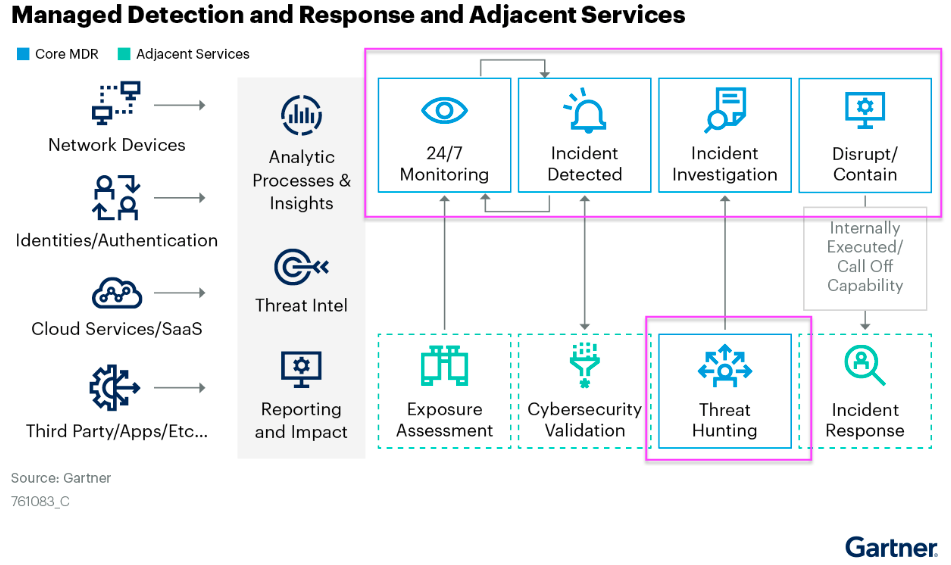
Market Guide for Managed Detection and Response Services 2/14/2023 ID G007610831
The core functions of an MDR solution are: 24/7 monitoring (SOC), incident detection, threat hunting, incident investigation, and the ability to Disrupt\Contain an issue. Also important is the ability to ingest data from different sources.
Government compliance is another compelling reason to consider an MDR solution. This is the pending requirement from the SEC as of March 9, 2022:
“Requiring registrants to disclose material cybersecurity incidents in a current report on Form 8-K within four business days after the registrant determines that it has experienced a material cybersecurity incident." Also added would be:
- When the incident was discovered and whether it is ongoing
- A brief description of the nature and scope of the incident
- Whether any data was stolen, altered, accessed, or used for any other unauthorized purpose
- The effect of the incident on the registrant’s operations
- Whether the registrant has remediated or is currently remediating the incident
Prerequisite: A company would need a near or full 24/7 detection and response capability, along with a level of forensics, to be able to properly discover, react, and then report this within a 4 day time frame.
Proposed New Rule: Cybersecurity Risk Management, Strategy, Governance, and Incident Disclosure
If this legislation is passed, the implementation of an MDR solution would provide these capabilities as well as others to ensure compliance.
Summary
Across the MDR market, it's important to assess your vendors thoroughly to understand the use-case coverage that they can provide to your organization. Basic tenets of log collection, monitoring, and 24/7 analyst coverage are commonplace. To determine the true ROI and usability of any MDR offering, look beyond basic pillars and evaluate any additional elements of their service in comparison to your current security controls and what a standard MDR would bring. For example; in the case of QOMPLX’s solution, the value-add of first party attack surface monitoring and identity risk analytics across on-prem and cloud (with integrative response capabilities back to existing EDR investments) demonstrates two additional coverage categories along with additional services to a pre-existing investment.
1 Gartner, Market Guide for Managed Detection and Response Services, Peter Shoard, Al Price, Mitchell Schneider, Graig Lawsone, Andrew Davies, Published 14 February 2023
Disclaimer
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally and is used herein with permission. All rights reserved.





